Note: Credits for gathering all the methods goes to Crazy Greek’s cybersecurity blog collection. We rewrote their original post to fit our readers needs.
Instagram was launched back in 2010 and has since then grown to become one of the most successful social media platforms. In 2012, Facebook acquired Instagram which led to an exponential increase in the platform’s user base. By 2020, Instagram prides itself with over one billion daily active users.
Simply called IG or The “Gram” by most of its users today, Instagram’s rise and complete takeover in the social media world can be attributed to many factors, especially its intuitive user-friendly interface and extended functionality. You can now share your photos instantly on Facebook straight from IG with a single click. How convenient?
Instagram provides an easy and excellent medium to keep the conversations going with your loved ones on the go. It makes it even easier to keep an eye on what’s happening with your favorite celebrities, minute by minute! Millions of IG users across the world are sharing their stories and other details of their lives through the highly interactive visual platform.
However, just like everything else that relies on technology, Instagram has its own share of shortcomings too. For instance, the IG team is always updating the platform to make it even better and more efficient but unfortunately, most of the updates end up creating user-based hitches. How many times have you been told to update the IG app on your phone if you want to continue using it? I’ve been in IG for several years and have even lost count of the number of times I have had to update the app to log in again.
The Password Issue
What’s the most common problem encountered by Instagram users? Lost password, of course. There are many reasons why people forget or “lose” their passwords. For example, very few of us today ever bother to write down our passwords on a notebook after signing up for any online service let alone IG. It’s just one those things we take for granted until the unexpected happens.
Rather than note down our passwords, we find it easier to use a generic password across multiple online accounts and tap or click “save” on our phone’s autofill function. Whatever happened to privacy and security? You’d be horrified by the level of total disregard for cybersecurity that exists on social media platforms today. Criminals only need to steal your smartphone or laptop to access all your “autofilled’ accounts.
I Can’t Log Into My Instagram Account!
If it hasn’t happened to you yet, you probably know someone who couldn’t log into their account after forgetting their password or getting their IG account compromised. There are many reasons why you could have forgotten your password, such as losing your phone, bought a new one, or crashed the phone. If you are locked out of your IG account, you can’t log in or even access your profile and photos. Now in this age where our lives almost depend on social media, getting locked out is one thing you wouldn’t even wish on your worst enemy.
The Solution – Hack a Way Back Into Your Instagram Account
The good news is that it is now possible to work around Instagram’s security protocols and regain access to your account, thanks to innovative products created by clever software developers out there.
Let’s look at the top four methods that you can use to hack into an Instagram account and regain access to your followers, messages, stories and photos.
NOTE: Disclaimer for Reading This Article
This article contains 4 practical ways of hacking an Instagram password. After reading the article, you’ll be equipped with sensitive knowledge, with the potential to use the knowledge for malicious intentions. The authors of this article, carry no liability for the way you’ll assimilate, use, or distribute this information. Hacking someone else’s account is not only a criminal invasion of privacy but a federal cybercrime that you can be prosecuted for. Keep that in mind as you read on.
Below are the top 4 methods you can use to hack Instagram password. These techniques are still working successfully in 2025.
Jump to The Methods Quickly:
1. Hack Instagram Account Using BruteForce
2. With Phishing Techniques
2.1. How to Create Instagram Phishing Website
3. With a Keylogger
4. By Password Guessing
1. Hack Instagram Account Using BruteForce Method
“Brute Force” is a technique in which you use specialized hacking software to crack the password of your account. Brute force techniques in the past relied on uploading a .txt document that contained a huge list of frequently used and updated passwords into an user’s browser. The software would then run through a list testing each password until it got the right character combination. This was often a hit and miss process but would eventually crack a password after thousands of trials.
Brute force password cracking programs were quite popular in the past until people and companies started using specialized characters, 2-factor authentication, and complex password generators in their passwords.
Introducing IGHacko App
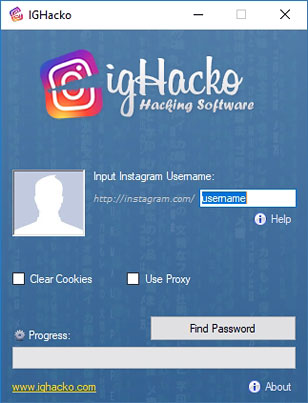 The efficiency of the brute force method was significantly reduced by the introduction of special characters. This opened a new opportunity in a cracking software industry. Developers created a number of tools most of which can still be downloaded free of charge.
The efficiency of the brute force method was significantly reduced by the introduction of special characters. This opened a new opportunity in a cracking software industry. Developers created a number of tools most of which can still be downloaded free of charge.
A good example is the IGHacko tool which contains a huge built-in database of commonly used passwords. The list is regularly updated by its developers, which makes IGHacko one of the most effective password crackers today.
Some of the key features of IGHacko include:
- It automates the complex process of running lists of passwords to hack your account
- Stealth operation – the program runs discreetly in the background, hiding your real IP address from ISPs. The developers use new proxy IPs every week.
- It automatically clears cookies from your browsers once the job is done to keep its operations covert and leaves no footprints.
The cracking efficiency of IGHacko depends on factors such as your Internet speed, computer’s CPU power, and password strength. A password with special characters ($%&? Etc) will obviously take longer to crack but how many times have you included such characters in your IG password? The fewers numbers or letters the target password has the easier it is to crack. You can run IGHacko on PC, laptop, smartphone and tablets. The program also works with all operating systems including iOS, Android, and Windows.
2. How to Hack Instagram With Phishing?
Professional hackers and cybersecurity experts state that phishing is the easiest method of hacking any account. If you’ve previously searched for password hacking methods online you must have come across phishing due to the method’s high success rate and proven reliability.
So how does phishing work? Well, it’s quite simple. The hacker will create a fake Instagram login page and direct people to use the fake page. The page is actually a back door system that sends your details to the hacker before redirecting you back to the real Instagram website. When an unsuspecting victim logs in via the page, they release their username and password to a hacker. In most cases, you won’t even know that your account has been compromised until it is too late. Instagram phishers control the accounts they acquire in two ways, namely via stealth mode or owners mode.
Account Control via Stealth Mode
In stealth mode, a hacker doesn’t change anything in your IG account. They won’t change the password or lock you out but choose to simply hang around watching and monitoring your activities behind a shadows, waiting for the right time to pounce and implement whatever strategy they have in mind. They can sit in stealth mode for years waiting for the best opportunity to occur before they strike. For example, they’ll wait for you to grow your account until you’ve gained a huge number of followers and become an influencer, then send DM’s to your followers requesting for their personal details for ulterior motives.
Account Control via Owners Mode
In this mode, a hacker gets your password, gains access to your account, changes the password, and locks you out. They’ll then circumvent IG’s security protocols and disable you from accessing the account completely. This is especially common with accounts with large numbers of followers. Such accounts can be sold for a high price on the dark web.
Creating an Instagram Phishing Page – Step by Step Guide
Phishing is quite common today, which is why we thought it’s helpful to give you all the information you need to know about this hacking method. You can also create a real phishing page by yourself to see how it all looks like in reality. Let’s show you how it is done to help you understand how the pages look like and possibly avoid you getting hacked by this technique in future.
To create a phishing page, you’ll need:
- A web hosting account (Paid is a much better option, but sometimes free ones can work too).
- Internet connection, obviously.
- And an ig_login_page.rar file which you can download and save on your desktop. You’ll also need to have the WinRar program to open the file. Most people have WinRar installed but if you haven’t downloaded it already, you can get it from its official website, www.winrar.com (Free plan will suit just fine).
Password to open downloaded .rar archive is”gowiper.com”.
Once you have the items mentioned above, you can start building your fake Instagram login page through the following steps:
- You need a web hosting account. A paid hosting account is more preferable but you can still get a free one at www.000webhost.com. Just keep in mind that 000webhost will ban your free account if they realize you are using it for phishing but it is free after all. Choose a smart website name that you’ll send your potential victims to. It has to be as real looking and convincing as possible. A good example could be something like “myigpage.”
- Waiting for an email from the web host and confirm your email. It may take as much as 8 minutes or less.
- Navigate to your account and choose the option “Upload Own Website”
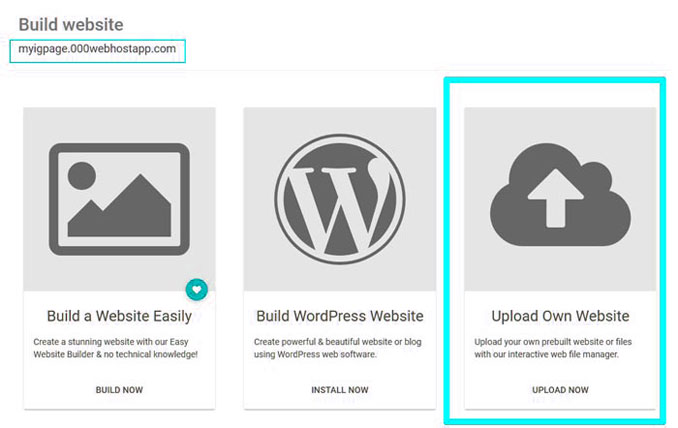
- Extract the ig_login_page.rar file and upload all the 11 files in the folder to your page. (If you’re using it on a paid hosting, folder where you have to upload these files is called “public_html” and you can find it by going to your cPanel > File Manager. Then you will find it inside. If there is a file already called “Index.html”, delete it before uploading those 11 files.

- Your phishing page will be created after you upload the files. You can check it by visiting your site’s link on a web browser. It should look like this:
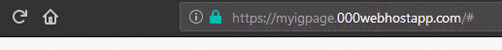
The link should send you to a fake Instagram login page if you did everything right.
- The next part is to send your victims to the fake login page. You’ll need to use your creativity and imagination to drive them to the fake login page. You could, for example, send them an email saying something like: “We’ve noticed suspicious activities on your account. We believe someone attempted to hack your account using your password. Log in via this Link using your password to verify that you are the real owner of the account.” This link will obviously lead to your fake phishing page. You can always come up with more creative ways to make them log in via your fake page.
- When the person enters their username and password in your fake Instagram login page, you’ll be able to see the information simply by typing: “/password.html” at the end of your page’s URL in any browser.
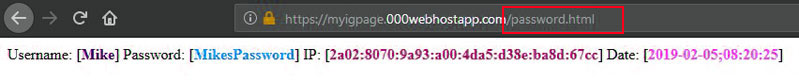
With this method, you can set up a phishing page in a few minutes and get a password of anyone who logs in via a fake page.
NOTE: If you’re using a paid hosting, then there is no a free domain (Like in this example “myigpage.000webhostapp.com”). You will have to register a “real” TLD (Top Level Domain) to use it with hosting. Domain is where your website is hosted. You choose its unique available name and extension, like “com”, “net”, “org” & others.
An approximate price for TLD domain is usually somewhere about $10 per year.
Approximate price for paid hosting is few dollars per month.
Hint: Always keep an eye for discounts and coupon codes where you can get domains and hosting for much cheaper, especially if you never registered anything before in certain companies.
3. How to Hack Instagram Using a Keylogger?
Keylogger programs are another popular way of working around Instagram’s security and gaining access to password-protected accounts. It is quite easy and fast to hack an Instagram account using this method. A keylogger is a software application that can spy information from the activities of your victim’s keyboard and save a data for later use in a file. So when your target logs in to IG using their credentials, a keylogger software collects an information and saves it for you.
Let’s look at the top three mobile keylogger software applications of 2023:
- mSpy
The leading & most popular mobile spying tool as of today, The mSpy is rich of features and has very user friendly interface which are two main reasons why it attracts so many customers.
mSpy Features:
- Works on iOS & Android
- Undetected Tracking System (Without others knowing they’re being monitored)
- Keylogger built in – See everything what others type on their phone
- SMS/Facebook Messenger/WhatsApp/Instagram/Viber/Snapchat/Telegram & other messaging apps monitoring
- GPS Location Tracking
- Check all Outcoming/Incoming Calls
Get mSpy tool by clicking the button below.
By using mSpy tool, you’re agreeing with their official disclaimer:

- iKeyMonitor
This is a top keylogger program that can record everything your victim types on their iOS or Android mobile device. It will even send an information to you online, which eliminates a need to access your target’s mobile device. This keylogger is a paid service but comes with a 3-day free trial. Use the trial period to get the data you need.
You can use iKeyMonitor if you have an Android or iOS device. To get iKeyMonitor, go to the official website. This keylogger is actually not free but there’s a three-day free trial for you to test it out.
How to Use iKeyMonitor:
- Buy or download a free trial of the app from the official site – www.ikeymonitor.com
- You’ll need to navigate to the Settings > Security in your phone and allow downloads from Unknown Sources before you can download the application.
- Install the app discreetly on a victim’s mobile device
- Configure the app on the victim’s phone by switching on a “Keystrokes” option
- Delete the app icon to ensure that it runs in stealth mode without your victim knowing it
- You can then log in to the application’s web dashboard with your credentials
- After some time go to the app’s “keystroke logs” option on the home screen where you’ll find a list of keylogging data from a target’s device
You can search manually a data from a victim’s phone to identify their Instagram password. iKeyMonitor is a paid app but comes with a 3-day trial period.
- Spyzie
If you are looking for a cheap but effective method of hacking any Instagram account, then try Spyzie. It has a keylogging feature that gives you access to the keyboard keys that your target types on their PC or mobile device. The tool will give you a list of words typed by a victim including their password. You can then use the information to log into their IG account and access everything including photos, access to their followers, read messages, check their past IG stories, delete pictures, and even block people. You get full control of the account. It is an effective tool when you want to hijack an Instagram account.
Using Spyzie:
- Create an account at spyzie.com and set up your account
- Enter a phone number of your target
- For Android phones install the Spyzie Android app in the root of your target’s phone. Read the Spyzie Android Tracking Guide to know how you can do this.
- For iPhones, jailbreak the victim’s phone and install the Spyzie iPhone App. Read the Spyzie iPhone Tracking Guide to know how to do it.
- From the Spyzie control panel, you can access the keylogger tab on the left-hand side and find all the keys that your target has pressed on their phone.
Spyzie is unlike other keylogger programs because of its features and stealth mode. As soon as you install Spyzie on a target’s phone, the app’s icon will be automatically deleted and run behind the scene undetected.
4. Guessing a Password to Hack an Account
Despite all the frequent warnings we get reminding us to change our passwords after every few months and always ensure that we use hard to detect random-generated passwords, you’d be surprised by a huge number of people who still ignore this basic Internet security protocol. You could even be one of them. Do you use the same password in all your online accounts? How long have you been using the same password in IG? Six months? One year?
According to SplashData, one of the leading software security companies today, here are the top 25 most common passwords used by more than 70% of Internet users today. If any of your personal passwords is in the following list, we advise you to change it immediately.
Here are the top 25 most commonly used passwords today as listed by SplashData:
- qwerty
- 123456
- password
- 12345678
- 12345
- letmein
- 123456789
- iloveyou
- admin
- football
- monkey
- welcome
- login
- 1234567
- abc123
- dragon
- passw0rd
- starwars
- 123123
- master
- freedom
- hello
- whatever
- trustno1
- qazwsx
If an account you want to hack belongs to a person you know well, you could try to use their birth date, names of their family members, or even a name of their pet. Studies show that over 60% of Internet users use birthdates and names of their family or pets for passwords. There is a good reason for this. Nobody ever prepares a password to use in any online form in advance. The request to enter a password finds most people completely unprepared and the only memorable password they can find in a hurry is a specific birthdate or the name of a favorite relative or pet.
The Question of Privacy and Ethics
This article has covered four practical and working methods of hacking into an Instagram account, yours or somebody else’s. However, it is important to note that everything that you do with the knowledge that you now have is an important test of your character and moral standards. You should NEVER under any circumstances use the information we have armed you with to hack or steal other Instagram users accounts. This is a criminal offense.
The legal system in the United States treats online fraud as a serious cyber crime with severe penalties. Hacking and accessing another person’s Instagram account without their consent is not only fraud but an invasion of privacy and identity theft too. It is a criminal act that deserves severe punishment.
Today’s technology provides parents and employers with diverse ways of securing their families, assets, and businesses. This does not, however, mean that we should use technology for unethical purposes. It is important to first consider the legal and ethical implications of your actions before you download and install any third-party software program that can be used to spy or hack other people’s online accounts. If you are an employer seeking to monitor your staff more closely, we recommend that you seek legal advice before you install any spying software on your business assets.
These technologies offer tremendous values to employers and parents, helping them secure people, assets, and family members. However, it may be tempting to be unethical in your use of a software. Before you decide to install any third-party software on the phones and devices of your family and employees, it’s important to think about the ethical and legal ramifications of your decision. Parents can decide to use the methods and apps discussed in this article to monitor their children but beware of the consequences of such acts. The best way to do this is by informing your kids of your good intentions before you install the apps on their phones. Otherwise, you risk losing their trust and respect if they discover that you’ve been spying on them.
Final Thoughts – Avoid Getting Locked Out of Your IG Account Again
You don’t have to be locked out of your personal Instagram account when you can use the readily available technology to regain access. The free software programs and features discussed in this article are more than enough to help you hack your password and gain access to your IG account again.


